This tutorial will show you how to join Ubuntu to an Active Directory Domain quickly and easily, this will allow domain users to logon using their domain account and allows the use of Kerberos authentication with tools such as Ansible. Before I start I’m going to assume you already have a domain controller configured and setup with Active Directory Domain Services.
Start by using your favourite SSH client to connect to Ubuntu, once connected the first thing we need to do is configure the hosts file:
sudo nano /etc/hostsUpdate the hosts file so it looks something like this (I’m using Ubuntu as the name of my Ubuntu instance and lab.local as my domain address)
127.0.0.1 ubuntu.lab.local ubuntuSave and exit (ctrl+O, enter, ctrl+x)
Now we need to install the required packages to allow us to use Kerberos authentication. Run the following commands to get everything installed
sudo apt-get update
sudo apt-get install krb5-user samba sssd sssd-tools libnss-sss libpam-sss ntp ntpdate realmd adcliOnce installed we need to configure Kerberos so let’s edit the krb5 configuration file
sudo nano /etc/krb5.confThe top of your file should already show the default realm as your domain address (in my case it’s LAB.LOCAL) so you shouldn’t need to edit that. In the [realms] section add a new entry for your domain and point it towards your domain controller.
[realms]
LAB.LOCAL = {
kdc = dc.lab.local
admin_server = dc.lab.local
}Now go to the bottom of the file and add a domain realm to the [domain_realm] section
.lab.local = LAB.LOCALSave and exit
Now we need to update NTP so the time and date is syncronised with the domain, start by editing the /etc/ntp.conf file
sudo nano /etc/ntp.confAdd an entry at the bottom of the file for your domains address
server lab.localWe’re now going to syncronise with the domain, we can do that with the following commands
sudo systemctl stop ntp
sudo ntpdate lab.local
sudo systemctl start ntpWe can now start the process of joining Ubuntu to the domain, we start by discovering the realm – your domain address needs to be all uppercase.
sudo realm discover LAB.LOCALNow that the realm has been discovered we can initilise Kerberos. Make sure to use an account that is part of the domain and the address must be uppercase again.
kinit -V [email protected]We’re almost there now, let’s now join the realm – upper case domain address again here.
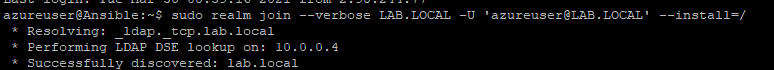
sudo realm join --verbose LAB.LOCAL -U '[email protected]' --install=/If all has gone to plan you should be greeted with a success message
Successfully enrolled machine in realmThere are a few more steps we need to do to finish the job, let’s start by editing sssd.conf
sudo nano /etc/sssd/sssd.confPut a # at the start of the use_fully_qualified_names line
# use_fully_qualified_names = TrueSave and exit and then restart the sssd service
sudo systemctl restart sssdWe can now enable password authentication so your domain users can logon
sudo nano /etc/ssh/sshd_configSet PasswordAuthentication to yes
PasswordAuthentication yesSave and exit and then restart the SSH service
sudo systemctl restart sshThe last steps are enabling home directory creation and adding DC Administration to the sudo privileges group.
sudo nano /etc/pam.d/common-sessionAdd the following line below session optional pam_sss.so
session required pam_mkhomedir.so skel=/etc/skel/ umask=0077Save and exit.
Now open the sudoers file
sudo visudoAnd add the following to the end
%AAD\ DC\ Administrators ALL=(ALL) NOPASSWD:ALLSave and exit as usual.
That’s it! You should now be able to login using your domain accounts. If you have any issues or questions feel free to leave a comment or get in touch with me on Twitter.